"ZTNA (Zero Trust Network Access) is the future of local network security"
Gartner, Inc.
Cyber criminals are continually inventing new methods to break into business networks in order to steal data and plant ransomware for extortion. Businesses have to stay one step ahead of the criminals by constantly updating the cybersecurity defenses. Cyber criminals have difficulty with direct network attacks because network firewalls have made remote network acess difficult. Most cyber attacks now rely on phishing to plant a Trojan virus onto a business computer which gives the criminal remote access to that computer and to the whole network making it easy to install ransomware. Unfortunately network firewalls do not block a phishing attack.
Zero Trust security technology has been developed to reduce the risk of a cyber attack that originates inside a network from an exploit such as phishing. The Authonet Zero Trust cybersecurity gateway authenticates both devices and users with 2-factor or 3-factor authentication. The Authonet Zero Trust cybersecurity gateway also sets strong rules for each user that determine what the user can access and what is not permitted, both in the local network and on the Internet. The gateway also monitors all network connections and alerts suspicious events such as multiple failed authentication attempts.

The Authonet ZTNA gateway protects the business network from a cyber attack, especially a password theft and phishing attacks.
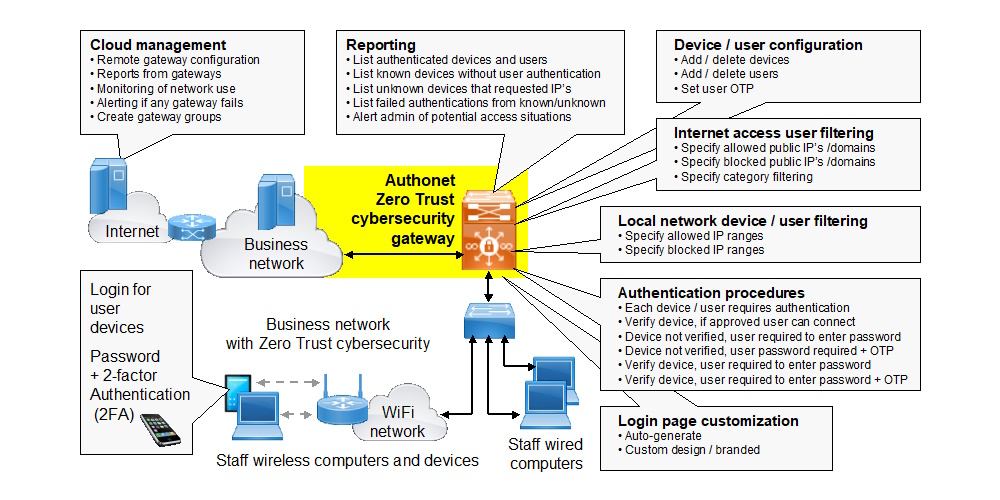
The Authonet gateway architecture has five principal functions listed here.
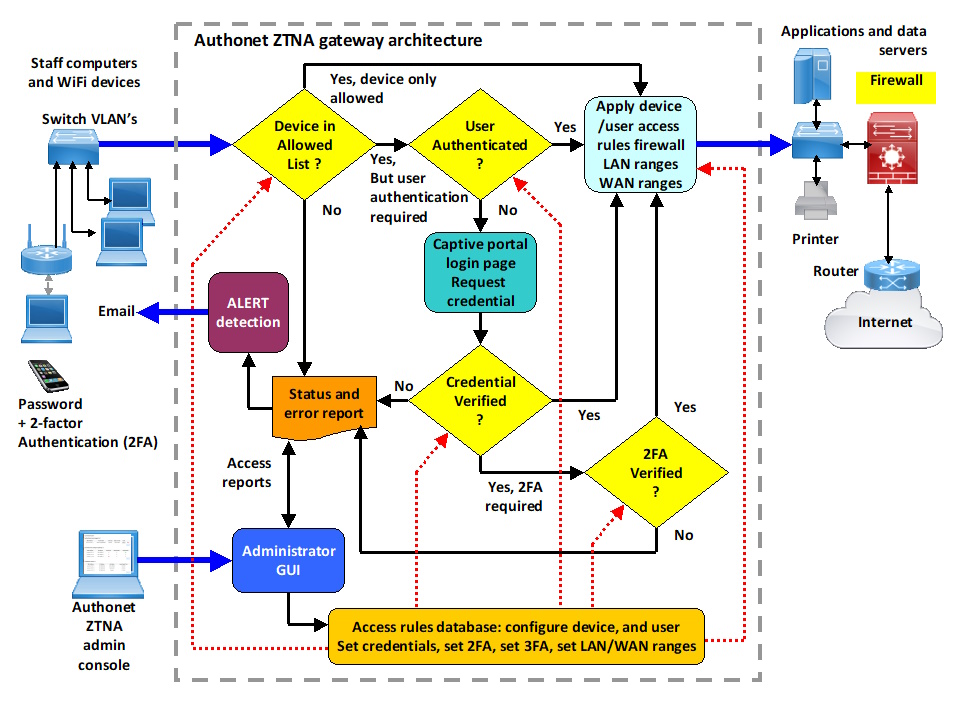
The diagram illustrates the internal architecture of the Authonet ZTNA gateway. All rules are configured into the database by the administrators dedicated out of band port.
The Authonet Zero Trust cybersecurity gateway imposes authentication rules on every device and user connecting to the network, and then imposes access rules on every device/user after successful authentication. The Authonet gateway requires configuring before it is operational. A login is required for all users and the login page can be customized.
Each device and user has a pre-programmed authentication rule which is a combination of device ID, user password and user one-time password (OTP). The rules can be in combination. For example any user may connect on an approved device, or a user may require 3-factor authentication (3FA), a known device, a user password and an OTP code. The purpose of the authentication process is to prevent access to the network by people who are not authorized. For example, a criminal might steal a password through social engineering. However if that password is associated with a 3FA account then the criminal will not get access to the network.
Once a device and user combination has been authenticated there are two levels of filtering rules.
The first level of rules are regarding the local area network. The IP addresses for the authenticated user are specified, the range can be blocked with the exception of specific IP's, or the range can be open with specific IP's blocked. This level of rules can be configured to prevent a criminal who has access to a Trojan virus getting access to a data server. For example, the user has access to an application server but only the application server has access to the data server.
Each device and user is configured with individual rules permitting privilege levels to be configured for devices and users.
The second level of rules is regarding the Internet. The range of public addresses can be open, with the exception of specific IP's/domains that are blocked. Alternatively the range of public IP's is blocked with the exception of specific IP's/domains that are open. Each user has individual rules.
Monitoring of network use is extremely important. Several reports are generated and include authenticated users, approved unauthenticated devices, unknown devices connected to the network, and failed authentications. Alerts can be sent to the network administrator when specific conditions are detected.
The initial configuration is made easy by a user friendly and intuitive graphic interface. The initial configuration takes some time but the installer will find the task easier than most firewalls.
An optional Authonet cloud management interface is available as a subscription. The cloud management interface is designed for IT departments that manage remote offices, and IT service providers who manage multiple clients. The management of multiple clients is facilitated with group configurations.
Two Authonet products are currently available. The A300 gateway has a throughput of 300Mb/s and is suitable for a business with 15 to 25 employees. The A1000 gateway has a throughput of 1Gb/s and is suitable for a business with 50 to 100 employees. The employee numbers are recommended however there is no limit for the number of devices and users that can be authenticated. There is a performance limit however based on the type of data traffic in the business. Authonet will be launching additional products suitable for both smaller and larger businesses. Authonet is committed to serving small and medium businesses and is aware of the need to provide high performance products with accessible prices.
A phishing attack is the most common method that a cyber criminal will use to plant ransomware and lock the business data. Phishing can be blocked, however restrictions have to be imposed on the use of the network in order to block the attack.
First it is necessary to understand the phishing attack process. The criminal will send many messages to business employees that impersonate a business or bank that the user may be familiar with. The message makes an urgent request to solve some problem by clicking a link, which installs a Trojan virus onto the computer. The computer user is tricked into installing the Trojan virus onto the computer and the user is not aware that the Trojan virus was installed.
After installation the Trojan virus calls the cyber criminal and the firewall lets it pass as it is an outbound message, like the user accessing a website. The cyber criminal replies to the message with program instructions. The cyber criminal programs the computer to access the data servers and the user is not aware that the cyber criminal is using the computer. The cyber criminal encrypts the server data files using the computer and as the last step puts a ransom message on the computer screen.
The phishing attack can be prevented by configuring the Zero Trust firewall parameters to specify what websites can be accessed. This may be a list of several hundred. All other websites are blocked. When the user clicks on the phishing link the criminals computer cannot be accessed as that IP address or domain is blocked. Although some effort is required initially to configure the Zero Trust firewall the risk of a phishing attack is eliminated.
