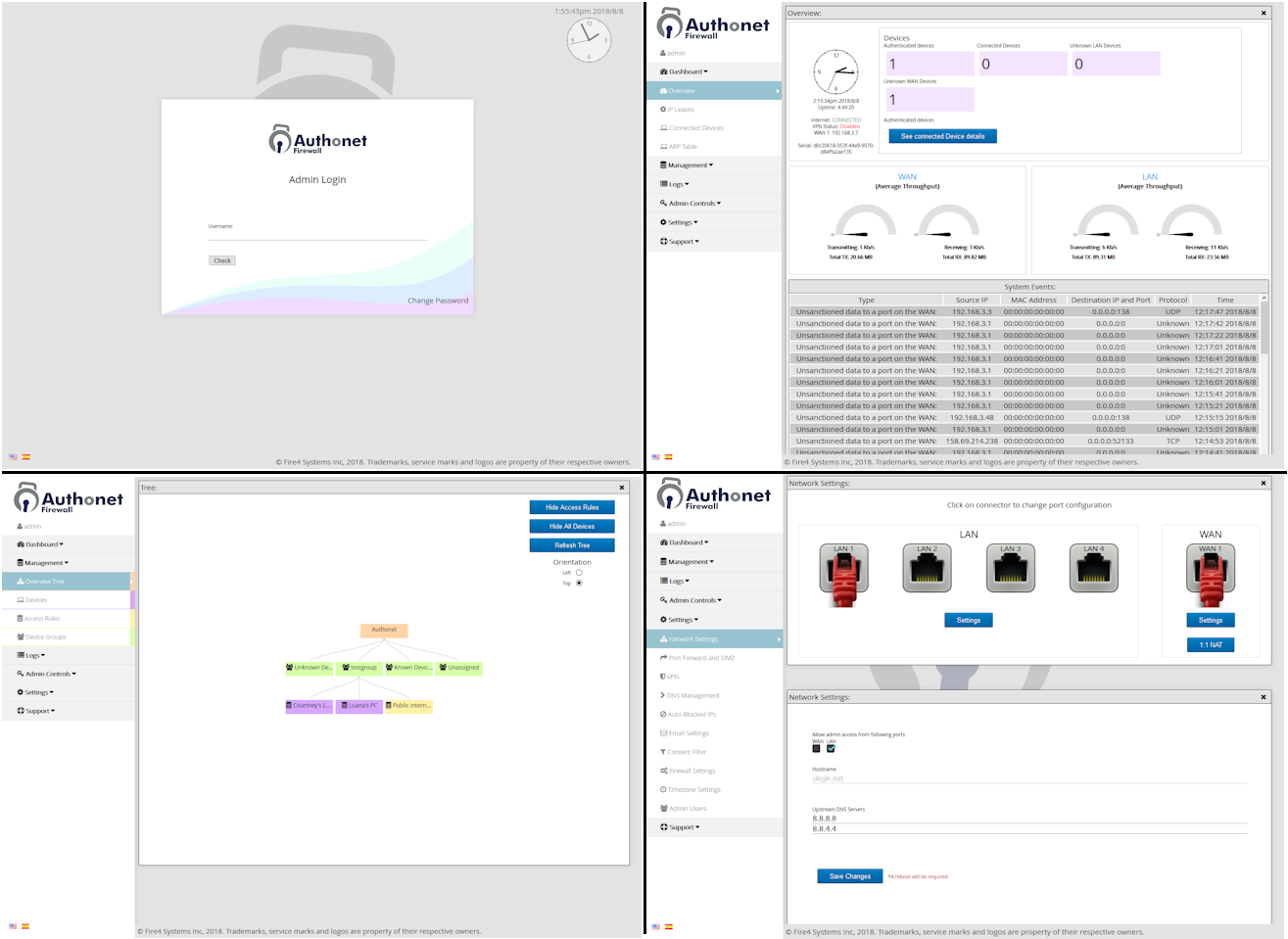
Authonet product range is easy to install and the simple user Interface ensures that each Authonet product is easy to setup and manage. No specialist networking skills are required; connect the Authonet product and take complete control of your business computer network cyber security.
Zero Trust means that any device or user connection is always authenticated before being allowed to access the network and is then monitored for the duration that the device is connected. Authonet Zero Trust security policies authenticate each device and user, and impose rules on local network and Internet access.

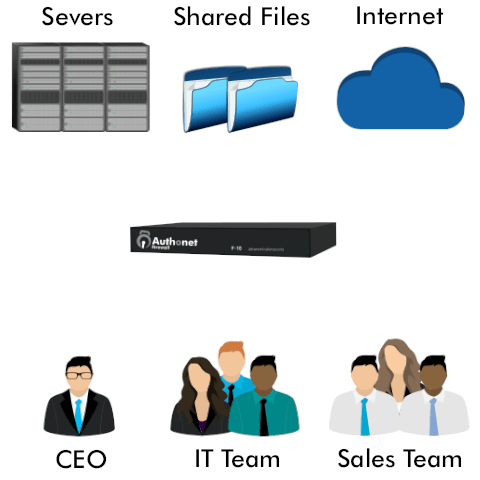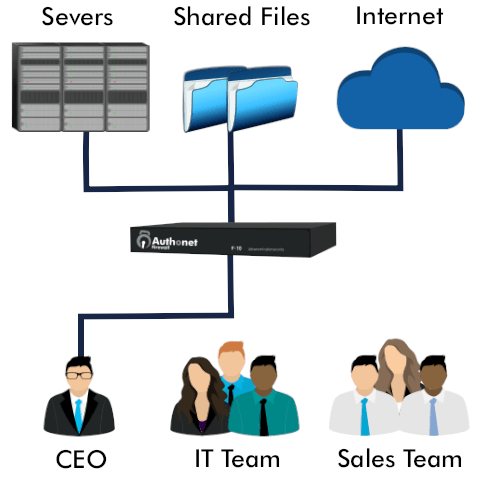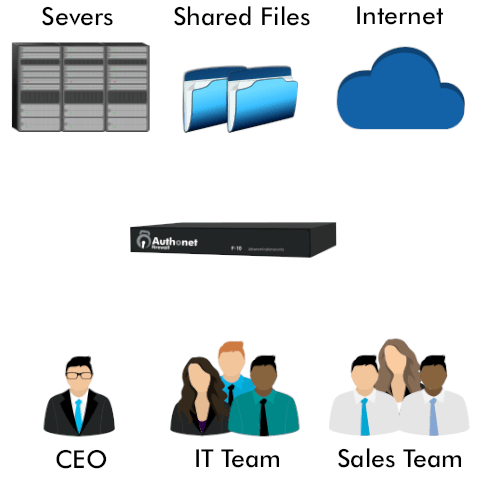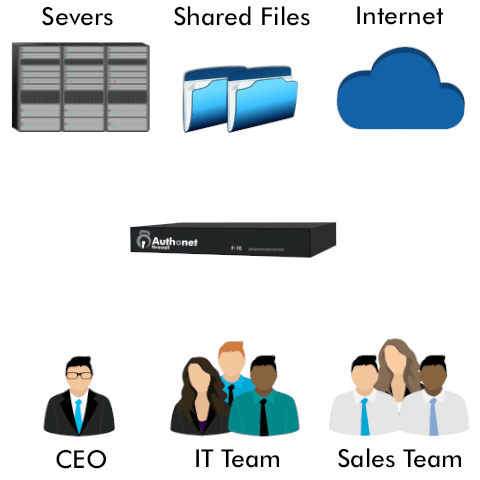
Most computer networks of small, medium and some large businesses are not managed or monitored. Access is free without security and the result is that the companies get hacked and become the victims of ransomware extortion. All business computer networks should require any access to be authenticated and network connections should be monitored for any attempted fraudulent access. Businesses can dramatically reduce the risk of a cyber attack with Authonet Zero Trust advanced cybersecurity. Cybersecurity has a cost but it is much less than the cost of data theft or a ransomware attack.
2-factor authentication is a very powerful tool to block hackers as it requires an access code to be sent to the users phone and entered as part of the verification process. For this reason most banks make the use of 2-factor authentication compulsory. Until now 2-factor authentication has only been available on security products that cost tens of thousands of dollars. Authonet Zero Trust security products all have multi-factor authentication, which can be implemented as 2-factor or 3-factor authentication.

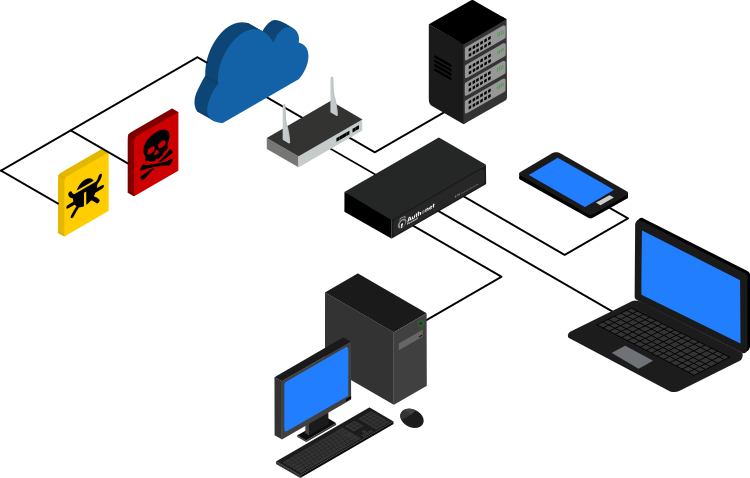
The Authonet Zero Trust gateway incorporates powerful tools that supervise non-stop access to the network. Devices are pre-approved for access and users can have single factor authentication, a password, 2-factor authentication login which is a password plus an authentication code from a mobile phone. 3-factor authentication can also be configured. The firewall functions include a range of special filters that determine what a user can and cannot access on both the local network and the Internet. A Trojan attack can be blocked by setting firewall rules.
The Authonet Zero Trust cybersecurity gateway provides all the services and features of Zero Trust products that cost tens of thousands of dollars more. Authonet has been able to offer Zero Trust cybersecurity in a compact and affordable package through the development of innovative technology that takes advantage of the latest high performance processors. Zero Trust cybersecurity is managed by the gateway product, which eliminates on-going charges that business have with other Zero Trust cybersecurity products. An optional cloud subscription is available for IT departments and managed IT service providers that permits multiple sites to be managed and monitored through one screen.

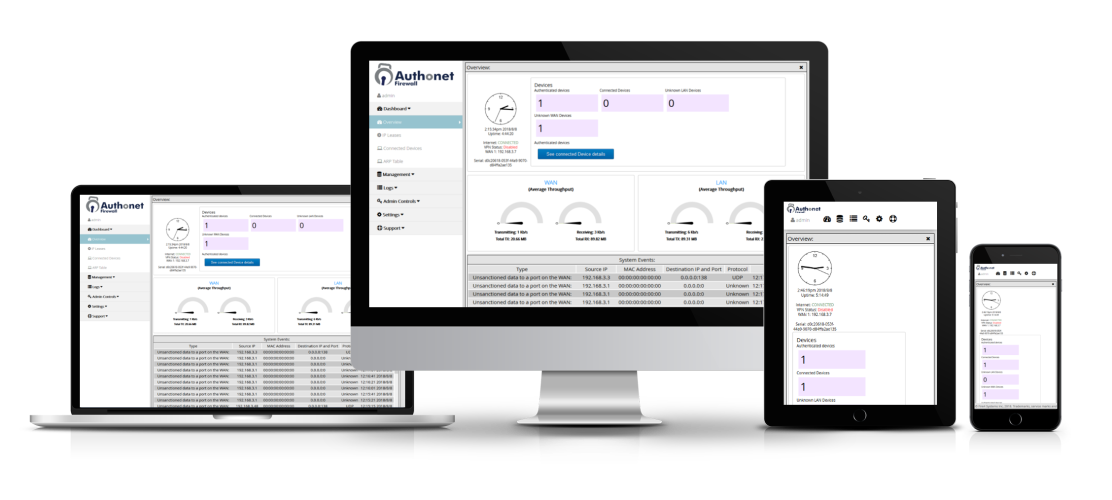
Authonet cloud management is an optional service that permits remote configuration and monitoring of one or more Authonet products. Group management permits several products to be managed as a group. The Authonet cloud is a valuable tool for managed service providers and for IT departments that have several Authonet products deployed.
Authonet endpoint security products generate four reports. The first is a report of authenticated devices and users who are currently connected to the network. The second is a report of connected devices that are approved but currently not authenticated. The third report lists devices that are not recognized but are connected to the network and the final report lists authentication attempts that have failed, which may indicate an attempt to access the network by a cyber criminal.


Authonet rules have an option to log an attempt to bypass a rule. The administrator can also be alerted of any attempted access to an area blocked by a rule. This is especially important for managed service providers who manage and monitor a number of clients and will add value to a 24/7 support plan.