While cyber-attacks and ransomware are increasing exponentially, businesses are not taking the necessary steps to protect from the attacks. Most business people know that attacks can come from the Internet and it is necessary to install a properly configured firewall to block access to the business network from the Internet.

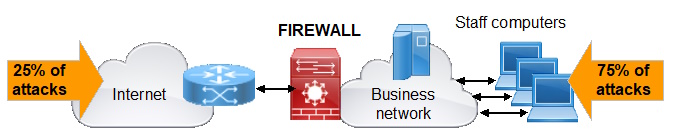
Many networks have a firewall installed as shown in the figure.

Analysis of #hacker attacks shows that approximately 25% come directly from the Internet while 75% are from within the network. With a #firewall installed between the Internet router and the business network most direct attacks are blocked, and therefore the dangers that remain are attacks from within the network.
Hackers trick employees to install a virus onto a personal or business computer that will give the hacker remote access to the computer. The virus calls the hacker so the communication bypasses the firewall, as the message is outbound. Firewalls can be configured to block outbound messages but this configuration is not common. During the time that the hacker has access to the computer, the computer user is not aware that the hacker is using the computer. The hacker uses the computer to access the business databases and can steal data or lock the database with ransomware and demand a payment in Bitcoin to release the data. Every computer that connects to the network should have anti-virus software that is kept up to date as this is the first line of defense against an attempt to install a virus.
Hackers use several tricks to fool the employee into installing a virus on the computer they are using, the most popular are:
The computer can be protected from a business email attack by filtering the business email and removing links and attachments. The business then has to provide a secure message system for employees to share information. This type of security is standard practice for banks. Banks used to be the #1 target for hackers but now invest in good cyber-security technology.
A business can block access to malicious websites by subscribing to a service such as Cisco Umbrella (openDNS) which blocks sites by checking the domain and IP address when the user computer makes a DNS request. Cisco Umbrella maintains a database of malicious websites and verifies all DNS requests from browsers to block those websites that are identified as malicious. New browser versions use encrypted DNS, which prevents DNS filtering and blocking of malicious websites. At present businesses can block encrypted DNS requests forcing the browser to switch to non-encrypted DNS.
The employee computers are at risk when personal emails are read on the computer, as the business has no control of the email content. Hackers are likely to attack an employee’s personal email. Businesses can block access to all email server access from office computers.
The biggest risk to a business #network is the case where the business allows personal devices to be connected to the business network. This is called Bring Your Own Device (BYOD). The business has no control of personal devices and the devices are connected to home and public networks. It is possible that a hacker has already installed a #virus by the time that the device is connected to the business network and is waiting for the moment to attack.
Hackers target people who are known to be employees of business that they want to attack. In many cases the names of employees are posted on the business website./p>
Hackers can attack the network WiFi directly and easily crack the encryption when the information to be stolen has a high value. Defense contractors, healthcare and law offices are at the greatest risk. Individuals sitting in the business car park can #attack a business WiFi network. WiFi security encryption is easy to hack and the business does not know this is happening. There are YouTube videos that explain how to hack WiFi encryption.
Businesses can improve security protection against hackers by installing a second layer of security, called network #endpoint security. The end-point refers to the extremities or perimeter of the network where user devices are connected, and includes the WiFi network. The end-point security device is installed between the users and the business network.

End-point #security provides protection for the business from devices that are connected to the network. End-point security can implement several security protection functions. Some of these are listed below.
End-point security is installed in the network using an end-point security gateway that all devices will communicate with when connecting to the network. The gateway will authenticate each device onto the network. Any device that does not meet the authentication criteria should be blocked from the network. Any device that does meet the authentication criteria but later does not conform to the data access requirements should also be blocked from the network. The endpoint security may require daily updating as new types of attack and new viruses are discovered. End-point security is implemented with managed WiFi products.
End-point security requires any type of user access to be authenticated. This includes devices connecting to the WiFi network, wired computers and remote users who should be connecting through a VPN for security, where the VPN router also connects to the end-point security system. The VPN connection is especially important as many employees now work in a hybrid form that includes working from home. Remote access to the business network is an attack vector that a hack can use to gain access and so a VPN remote access is essential.
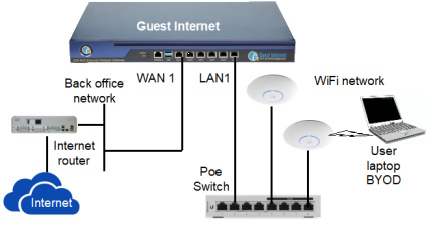
A secure business network with end-point security protection is shown in the next figure.

A business should consider moving applications to the cloud in order to increase the protection against a ransomware attack. Cloud systems are harder to hack as the cloud providers invest heavily in cyber-security. The business can wither switch to cloud based versions of applications currently in use, move business management to a different type of software that is available in the cloud, or migrate a custom software application that the businesses uses to the cloud.
There are specialized products that are simple to install with a low cost and cover many of the points required to implement end-point security and protect the network from hackers. An end-point security installation with a Guest Internet gateway is shown in the diagram below. The gateway contains the software required to authenticate users onto the network.
From the employee’s point of view, end-point security is a nuisance. Connecting to the network takes longer and the user may have to remember a password or wait for a 2-factor authentication code. The employee also has to be careful how the device is used to access Internet web sites as the device may become blocked by the end-point security.
The cost of keeping a network secure requires a firewall plus end-point security, with constant updating of virus profiles and other criteria. Data protection has a significant cost but not using data protection has a much higher cost when the business gets hacked with ransomware and then has to pay for the cyber-security.
Readers are invited to share this information with others. If any reader has a question regarding this information please contact us via our contact page.
Protect your business from an expensive ransomware attack. Unfortunately ransomware attacks have become a ...
Cybercriminals are attacking business IT infrastructure to steal and sell information, and for extortion using ...